Paliscade
Cybersecurity Adversary Threat Detection.
We develop use cases for information security operations to enhance your Incident Response, Threat Detection & Hunting capabilities by detecting malicious indicators of attacks from adversary's Techniques, Tactics and Procedures within your Enterprise environment.
How we help your Security Teams

Upscale your Security Operations
Elevate your security engineering capabilities with a repository of detection and threat hunting use cases to quickly detect adversary's Tactics, Techniques and Procedures within your organization's environment; so that you can focus on responding to real security incidents and improve on other security aspects, like automation and orchestrating your processes.
![]()

Engineering Focused
We aim to create an Executive Team of Threat Hunters, Security Engineers, Incident Responders, Analysts and Penetration Testers.
Together, we help engineer and produce use cases content to improve your threat detection and prevention capabilities for Security Information & Event Management (SIEM), Extended Detection & Reponse (XDR) and other custom solutions you use.
![]()

Continuous Support and Integration
Paliscade help our customers consult on gathering the appropriate log sources and required telemetries, then feeding it through our constantly evolving library of detection use cases that your tactical security teams can use for threat visibility.Each detection analytic content is mapped to one or more MITRE ATT&CK techniques and tactics, as well as the D3FEND Framework, where appropriate.Furthermore, we work with your operational teams to continuously optimize these use cases to keep them relevant and effective. We treat your cyber security investment as if they are our own.![]()

Accelerate Threat Detection
Leverage from a content library to address threat detection and use case analytics to improve defense capabilities against the ever-changing cyber threat landscape.

Build Content
Implement custom content on various SIEM solutions to reduce production time and costs on security engineering.
Hunt for Threats
Develop hunting hypothesis and detection rules to proactively hunt for artefacts instead of only relying on the re-active approach of responding to alerts.
Use Cases
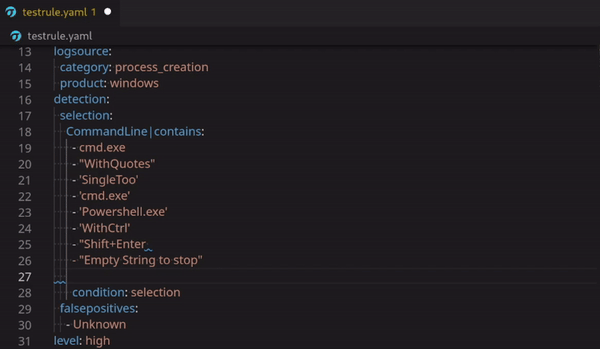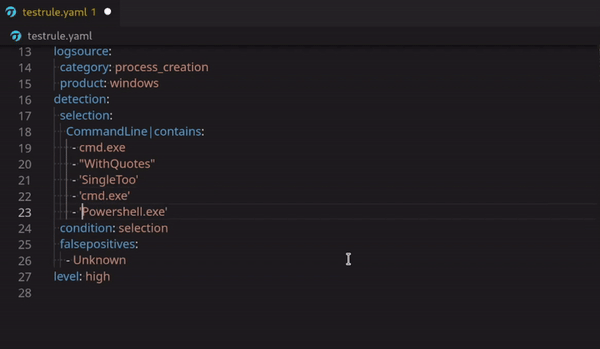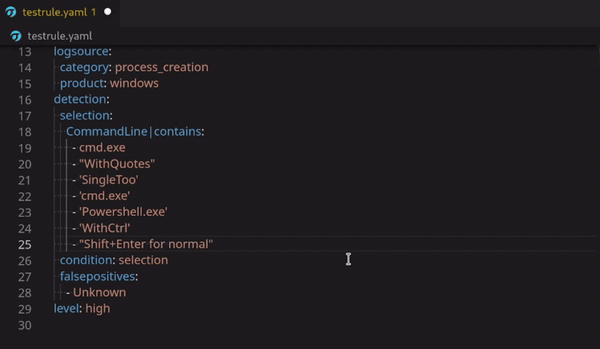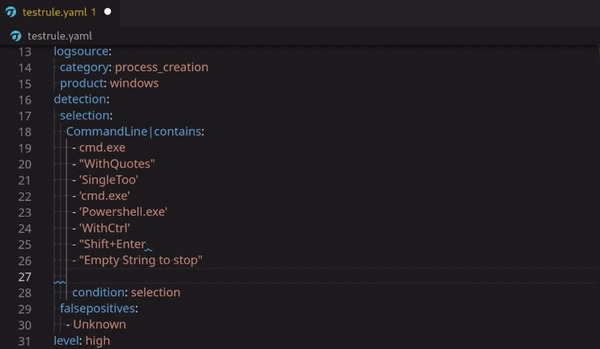
Possible Bind or Reverse Shell via Netcat
Technical Use Case (example) detection:
Netcat is one of the classic tools that threat actors used to establish a shell back to their remote hosts for command and control (C2) of compromised systems. This use case detects possible bind and reverse shell over a listening port that Netcat uses to listen for outbound connections from your compromised endpoint.
Kusto Query Language for Microsoft Endpoint Detection:
Syslog | where ((process.name =~ 'netcat' or process.name =~ 'nc') and ((network.direction =~ 'listening' or network.direction =~ 'outbound' or network.direction =~ 'outgoing') or (process.args =~ '-e' or process.args =~ '/bin/bash' or process.args =~ '/bin/sh' or process.args =~ '-nv')))
MITRE ATT&CK references:
- Command And Control
- attack.T1008
- Execution
- attack.T1059
- attack.T1072
Why custom threat detection?
Business Use Case:
Proactive Threat Identification: Threat detection engineering focuses on identifying potential threats in real-time, helping organizations to react swiftly and prevent data breaches or system compromise. Without effective detection use cases, attackers can exploit vulnerabilities before they are detected, leading to significant damage.
Continuous Monitoring: Having enhanced detection logic ensures continuous surveillance of your networks and systems, allowing for constant monitoring of the latest potential threats. This ongoing vigilance is necessary to catch emerging threats that may not be visible through traditional defenses like firewalls or antivirus programs.
Rapid Response to Attacks: Great detection engineering enables organizations to quickly understand the nature and scope of an attack. Once detected, appropriate response mechanisms (e.g., containment, eradication, recovery) can be triggered, minimizing the time an attacker has to exploit a vulnerability.
Compliance and Regulatory Requirements: Many industries are subject to strict regulatory requirements (e.g., GDPR, HIPAA, PCI-DSS) that demand the protection of sensitive data. Threat detection is often a key part of compliance, as it helps prove that an organization is actively monitoring its systems for suspicious activity, which is essential for audits and meeting legal obligations.
Resource Optimization: Effective threat detection engineering also helps you prioritize which incidents require immediate attention and which can be monitored. By filtering out false positives, organizations can focus resources on genuine threats, reducing noise and improving operational efficiency.
Our Network Partners
Paliscade partners with world-class leaders in Cyber Security.
